- Published on
Magento 1 Raveinfosys/DeleteOrders Security flaw
- Authors
- Name
- Niko Granö
- Github
- @NikoGrano
- Socials
- Address
Mail
P.O. Box 5
FI-01711 VANTAA
FINLAND- Company details
Other
VAT Registered
FI29067989

I have discovered possible SQL injection (CWE-89) on Raveinfosys/DeleteOrders extensions. This is extension to provide possibility delete orders. Like they describe it
Currently, Magento® doesn’t allow you to delete an order from the store. You can only mark them as Cancelled but can’t delete them from store. This extension allows you to seamlessly delete any order and other associated data such as invoice and shipment, creditmemos.
The Delete Order Extension comes with following options:
- To delete any order from the order list page.
- To delete any order from the order page.
- Mass action to delete bulk orders from admin order list page.
- Configuration option to select an order status that could be deleted from the store.
Fancy? Yes. Solid? Nope. Let’s see the code.
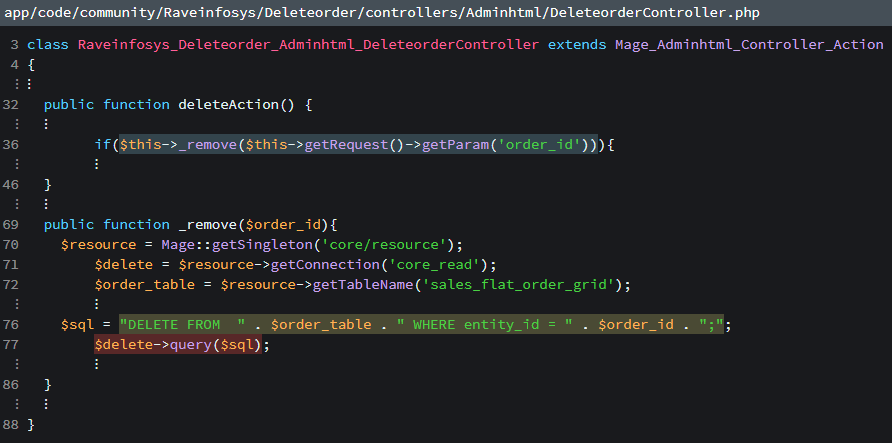
A-Haa! There we go. Perfect example how to make a injectable code. However, luckily this is exploitable only when logged in as admin meaning, users without admin login cannot exploit this.
Seems like little later they have been trying to update this and still again they have caused another injection.
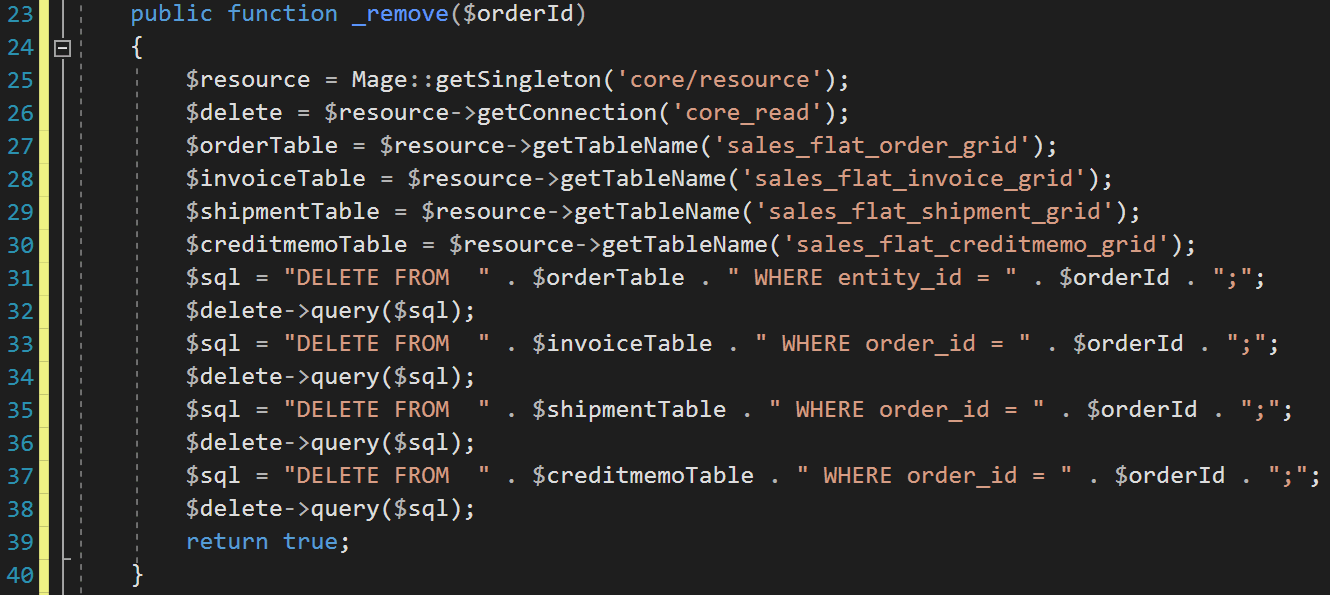
Shame shame…
Currently there is no public fix for the issue. Currently latest version is 1.1.2 and it’s having still issues.
Vendor of this module have published version 1.1.3 where they note this to be fixed. It’s highly recommended to use 1.1.3 to avoid injection.
You can find latest version of this extension here.
Other
I have created PR to magevulndb to report this issue. I encourage everyone working with Magento 1 to report issues here. This allows people to recognize security issues before it’s late.
Magento is an attractive target for payment skimmers and the number of attacks has increased steadily since 2015. In 2018, attackers shifted from Magento core exploits (eg, Shoplift, brute force attacks on admin passwords) to 3rd party software components. This poses a practical problem: there is no central place where one can (programmatically) find out whether a particular module version has known security issues. This repository is aiming to solve this issue. Please check it out!
Will personally highly recommend to integrate something like this into your CI/CD integration to make sure there is mo faulty modules slipping trough.